HTB Retired Box Walkthrough: Mirai
Mirai is a retired Linux machine that is rated as Easy on Hack the Box.
Mirai is a retired Linux machine that is rated as Easy on Hack the Box.
Hostname: Mirai
IP: 10.10.10.48
Operating System: Linux
Port Scan Results*
A simple nmap port scan nmap -vvvvv 10.10.10.48 yields the following ports:
22/tcp: ssh
53/tcp: domain
80/tcp: http
Further Enumeration*
Let’s go a little deeper with version numbers. We know it’s a Windows system and the name is a hint of sorts it seems. I use nmap -vvvvv -A -sVT 10.10.10.4.
22/tcp: OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
53/tcp: dnsmaq 2.76
80/tcp: lighttp 1.4.35
Methodology
Updated port scan and enumeration information:
22/tcp: OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
53/tcp: dnsmaq 2.76
80/tcp: lighttp 1.4.35
Let’s take a look at the website before we attempt exploitation.
Hmmm…nothing in the page source. Let’s see what gobuster can find.
gobuster dir -u http://10.10.10.48 -w /usr/share/dirb/wordlists/common.txt
Interesting, A Pi-hole. Using the name of this system as a hint, Mirai botnet logged into systems using default credentials. A quick search for default raspberry pi credentials landed me the combination of pi:raspberry from here. Let’s check to see if this is correct here using Medusa:
medusa -h 10.10.10.48 -u pi -p raspberry -M ssh
That works! Now, let’s try to login via SSH. ssh pi@10.10.10.48
Now let’s see who we are and if we can sudo.
Okay, we have sudo, so the path to root should be easy. Let’s get user first.
We’ll cd ~ then move to Desktop (could also cd ~/Desktop).
There’s user! Now, let’s sudo bash then move to root.
That’s not a flag (in the correct format)! Let’s check the USB Stick. We can check 3 directories for mounted external drives: /dev, /mnt/, and /media. Let’s check /mnt first.
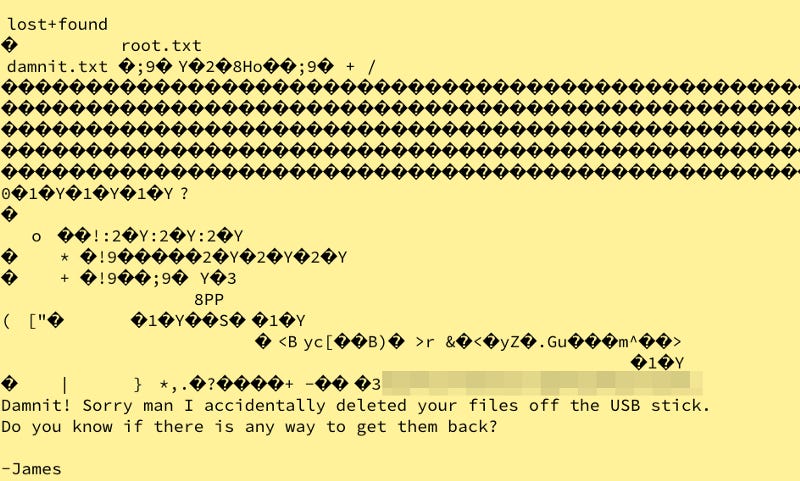
Nothing here, let’s check /dev. Quite a bit here. /dev/sdb is normally where a USB Stick may be. Let’s read this file
It’s a mangled mess. Let’s note the /media/usbstick mention and scroll down.
That’s dirty, but it looks like a flag.
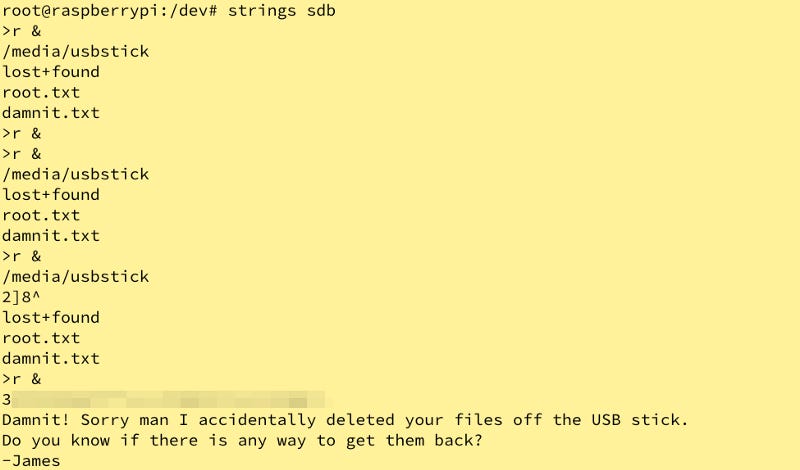
Note: Alternatively, we could have used strings on the file to see this more cleanly.
That’s all she wrote.
Findings, Sample Code, and Flags
Finding 1: The Mirai system is using default credentials that are publicly accessible on the internet.
Finding 2: The ‘pi’ user that is a default account is enabled under the same name.
Finding 3: The ‘pi’ user has sudo permissions.
Additional Actions
None.
High-Level Summary and Recommendations
C_3PJoe (the adversary) was commissioned to perform a penetration test of the host Mirai (the victim) in an effort to see what vulnerabilities existed within the system and determine what paths to exploitation existed. Through using default credentials (user name: pi, password: raspberry), C_3PJoe was able to gain access to the user as pi.
Once on the system, pi had sudo permissions that enabled the adversary to escalate to root-level permissions.
Recommend disabling default accounts and changing default passwords.
Tools Used
nmap
SearchSploit
Medusa
SSH
Other Walktroughs: